
Top 5 Cybersecurity threats to Estate & Lettings Agents 2021
Top 5 Cybersecurity threats to Estate & Lettings Agents 2021
Since the property industry routinely works with and transfers large sums of money, agencies are on every cyber criminal’s radar. As a result, it is not just property professionals and investors making money off real estate; cyber criminals are making money off it too. In fact, one third of estate agencies have experienced a cybersecurity attack in the last two years and in 2019 it was reported that attacks against property-related businesses increased by more than 100%.
We support many agencies across the UK and here are the most common threats we have seen first-hand affecting Estate and Lettings Agents:
1. Phishing
Phishing is a form of social engineering whereby an attacker sends a fraudulent message designed to trick the victim into revealing sensitive information. We work with many Estate and Lettings agents across the UK and have seen first-hand the rise in phishing emails.
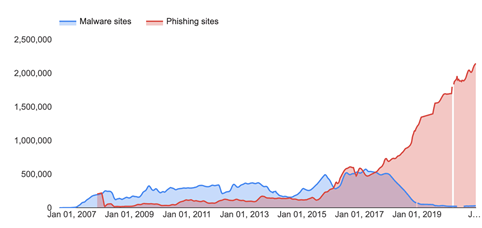
As per the below graph – taken from Google Safe Browsing data – shows the dramatic increase in phishing sites in recent months and how they have overtaken Malware sites as the most prolific unsafe sites on the web.
According to a report published by PWC, over half of the cyber security attached reported in 2018 involved phishing.
The two best methods of securing your Agency against Phishing attempts are Cyber Awareness training and enabling Multi-Factor Authentication.
2. Ransomware
Ransomware is a type of malware that threatens to perpetually block access to data unless a ransom is paid.
A report conducted by cybersecurity company Deep Instinct shows ransomware attacks increased by 435% from 2019 to 2020. Double extortion tactics became the new standard in ransomware, with the threat of data not only being encrypted but also exposed posing a major threat to organizational security and protection.
The pandemic and subsequent move to remote working, agencies have inadvertently widened their organizations attack surface making it easier for attackers to gain access to their systems to install ransomware.
Securing your business against ransomware is not an easy task, ultimately it requires a well-rounded secure network environment to prevent infection and next-gen Antivirus for detection and remediation. The best tip we can offer is to have regular security audits with a professional company. Completing your Cyber Essentials qualification is great first step.
3. Insider Threats
An insider threat is a malicious threat to an organization that comes from people within the organization, such as employees, former employees, contractors or business associates, who have inside information concerning the organization’s security practices, data and computer systems.
To block insider threats, agencies need to ensure that they have a strong culture of security awareness within their organization. This will help to stop insider threats caused by ignorance and help employees to spot early on when an attacker has compromised, or is attempting to compromise company data.
Also having strict IT policies in place, which include where staff can store or move data and outline the procedure for account creation and removals. The last thing you want is for a former member of staff to retain access to business systems after they have left the business.
4. Weak Passwords
Weak passwords are passwords which can easily be guessed by brute-force attacks. They are either common to many people or are short and not unique.
In 2019, the NCSC analysed public databases of breached accounts to see which words, phrases and strings people used. Top of the list was 123456, appearing in more than 23 million passwords. The second-most popular string, 123456789, was not much harder to crack, while the top five included “qwerty”, “password” and 1111111.
After an attacker has compromised a server containing usernames and passwords, they generally end up on the dark web – publicly available for other hackers to attempt to log into your systems.
Use the following tool to check if your password has ever been leaked onto the dark web – Have I Been Pwned: Pwned Passwords
5. Un-Patched Systems
A security patch is a change applied to an asset to correct the weakness described by a vulnerability. Every device that connects to the internet should be receiving security patches from the vendor as well as all the software installed on those devices.
Hackers love security flaws, also known as software vulnerabilities. A software vulnerability is a security hole or weakness found in a software program or operating system. Hackers can take advantage of the weakness by writing code to target the vulnerability.
The best fix for this is to monitor the patch status of all your devices and regularly check your systems are up to date. This is a time consuming job, so we would recommend outsourcing this responsibility to a managed service provider who has the knowledge and technical resources to fully monitor all your network devices patch statuses.
Interested in finding out more?
Get in touch with us today.
Comments are closed.