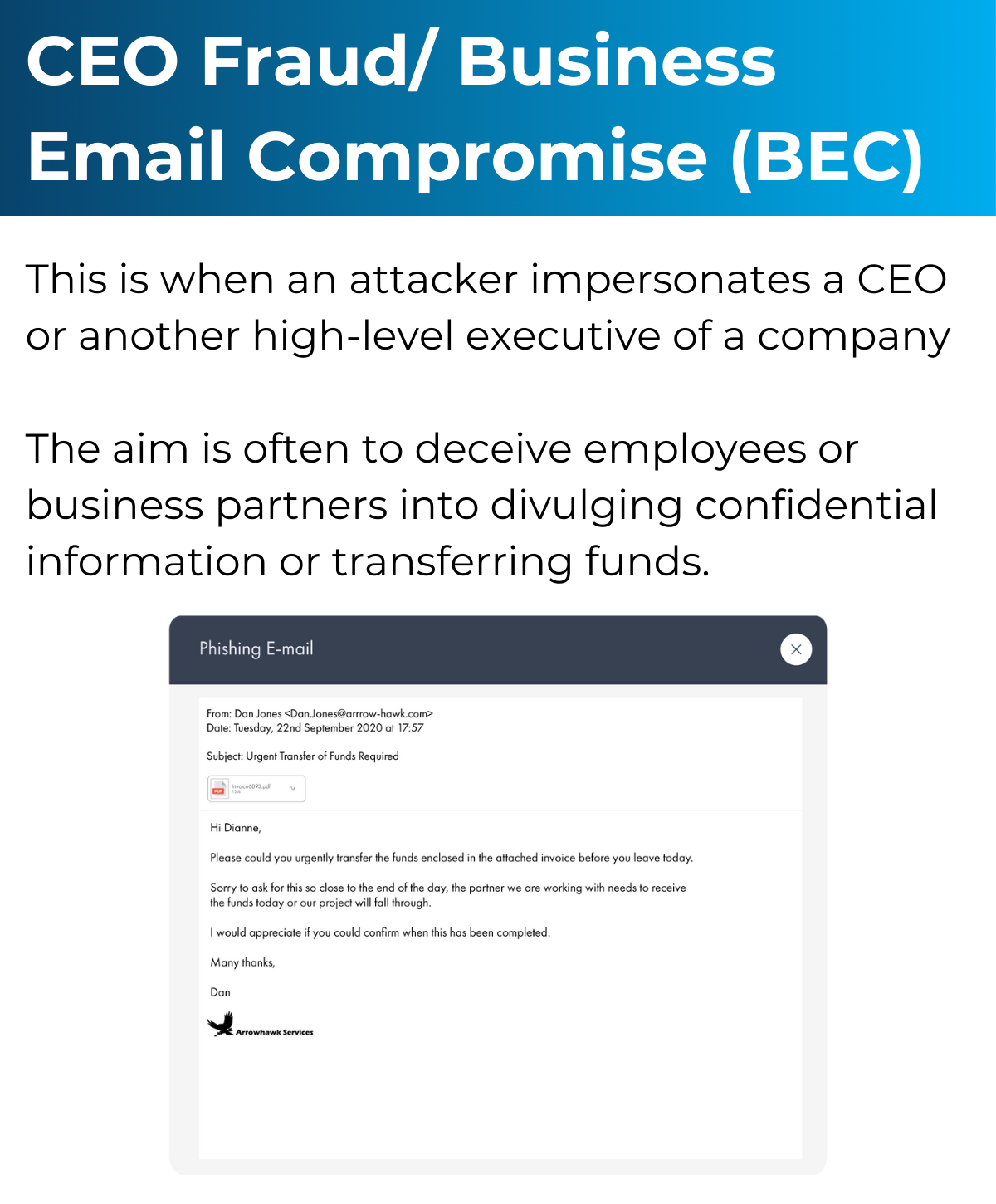
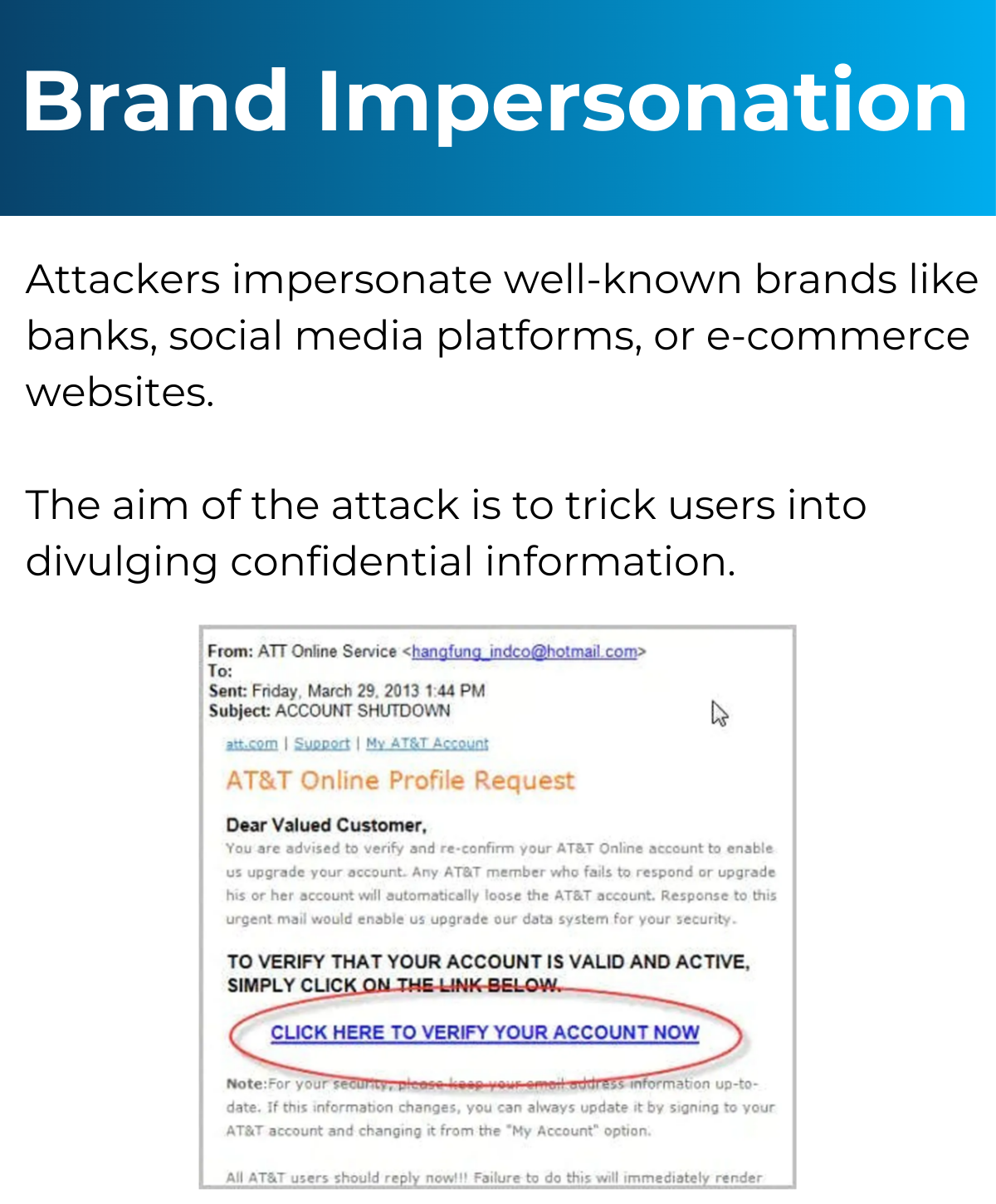
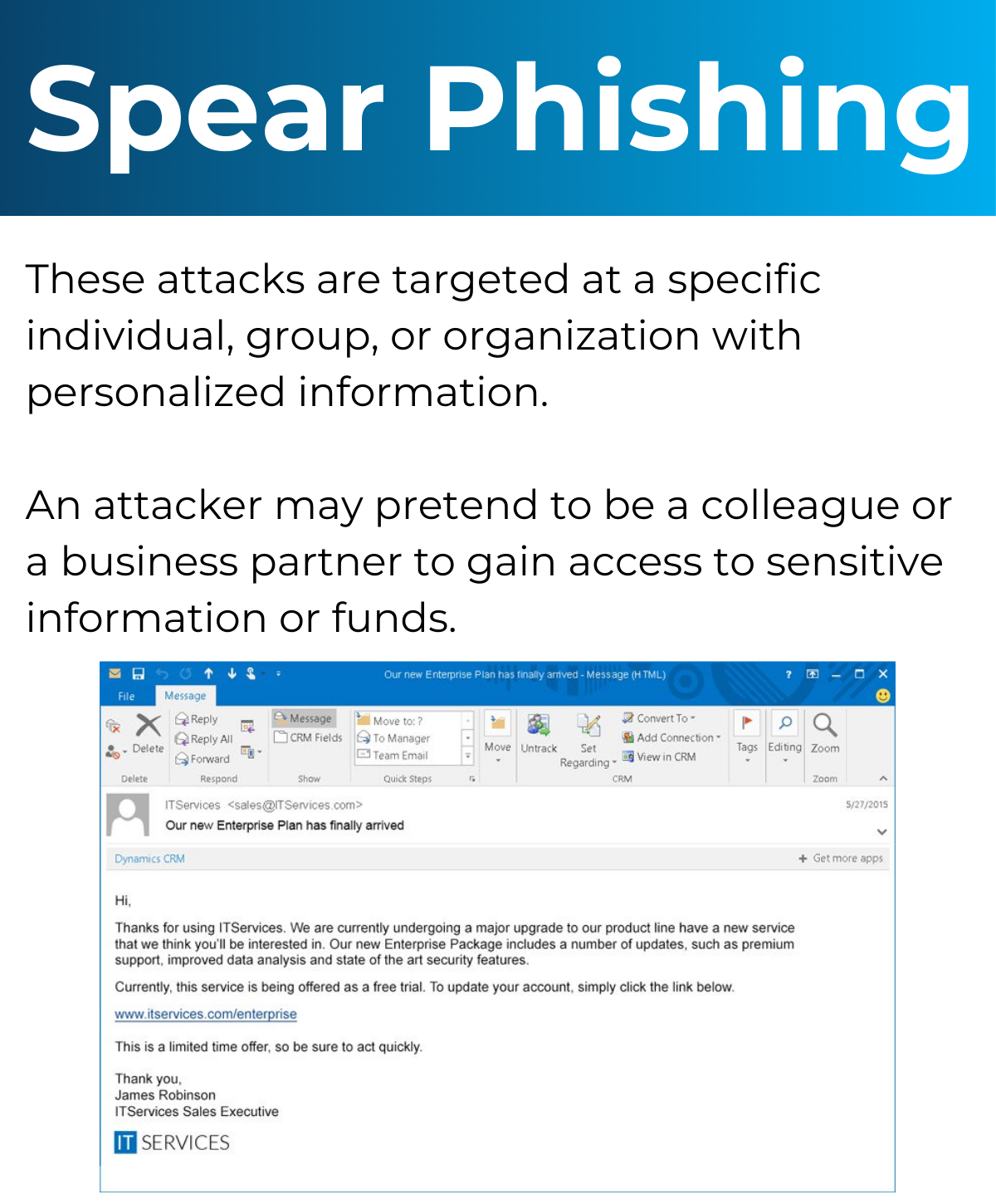
Simulated Phishing
Simulated Phishing is a key defence in the fight against hackers.
The most significant cyber risk to your business is the lack of awareness the workforce has about cyber-attacks.
With an ever-increasing, more complicated threat landscape, ongoing user awareness is a crucial component of a secure business.
-
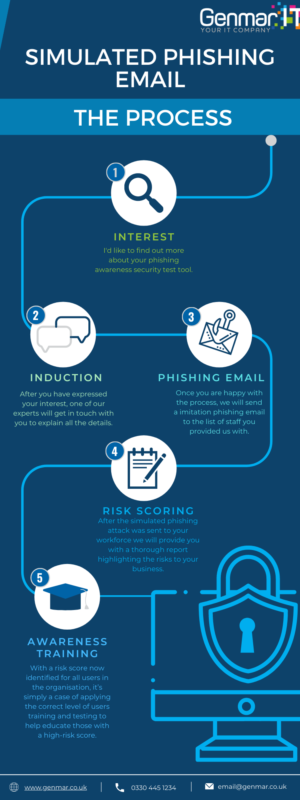
Simulated Attack
Simulated phishing attacks can help educate your staff on how to spot a fake email. There are a number of software solutions on the market now that will simulate a phishing attack on a group of users within your organisation. These simulated attacks can be planned in advance and play upon some of the most common security weakness that can easily fool someone into clicking the link in an email. Ongoing simulated attacks can be managed within the software and help build up a picture of where the risk might be in your business.
-
Risk Scoring
As part of the simulation, risk can be calculated against all individuals. If they open and then click on a simulated email, the system can keep score and track who is more likely to open future emails from unknown sources.
-
Continual Training
With a risk score now identified for all users in the organisation, it’s simply a case of applying the correct level of users training and testing to help educate those with a high-risk score.
The Benefits of Simulated Phishing
Increased awareness: Simulated phishing helps to raise awareness among employees about the risks and consequences of phishing attacks. This can help employees to be more vigilant and cautious when handling suspicious emails, links, or attachments.
Improved training: It can identify weaknesses in employee training, allowing for targeted training to address those weaknesses. This can lead to a more knowledgeable and prepared workforce.
Better response time: Simulated phishing can help organizations to test their response time to a potential phishing attack. This can help them to develop and refine their response plan to ensure that they can quickly and effectively respond to an attack.
Cost-effective: This is a cost-effective way to test an organization’s security measures against phishing attacks. Compared to the cost of a real phishing attack, which can be significant, simulated phishing is a relatively low-cost way to identify and address vulnerabilities in an organization’s security.
Risk Scoring
Both the risk scoring, and training should be an ongoing program in your workplace. The types of email phishing that get through many of the safety nets are always changing and having a workforce that is both aware of the threat and how to identify potential new scams is an investment worth paying for to help secure your business technology systems.
FAQ’s
Q: Why is simulated phishing important?
A: Simulated phishing is important because it helps organizations identify weaknesses in their employees’ ability to identify and respond to phishing attacks. By conducting regular simulated phishing campaigns, organizations can educate and train their employees to better protect themselves and the organization against real-world attacks.
Q: How does simulated phishing work?
A: Simulated phishing campaigns involve sending mock phishing emails to employees, often with a link or attachment that, if clicked, would lead to a simulated attack or training module. The organization can track who clicks the link or attachment and provide targeted training to those who need it.
Q: Can simulated phishing cause harm to the organization or its employees?
A: Simulated phishing campaigns are designed to be safe and non-malicious, but there is always a risk that employees may mistake a simulated phishing email for a real attack and take inappropriate action. Therefore, it is important for organizations to communicate clearly to employees that a simulated phishing campaign is taking place and provide training and support to ensure they respond appropriately.
Q: How often should simulated phishing campaigns be conducted?
A: The frequency of simulated phishing campaigns will depend on the organization’s risk profile and security posture. However, it is recommended to conduct campaigns at least quarterly to keep employees engaged and aware of the threat of phishing attacks.
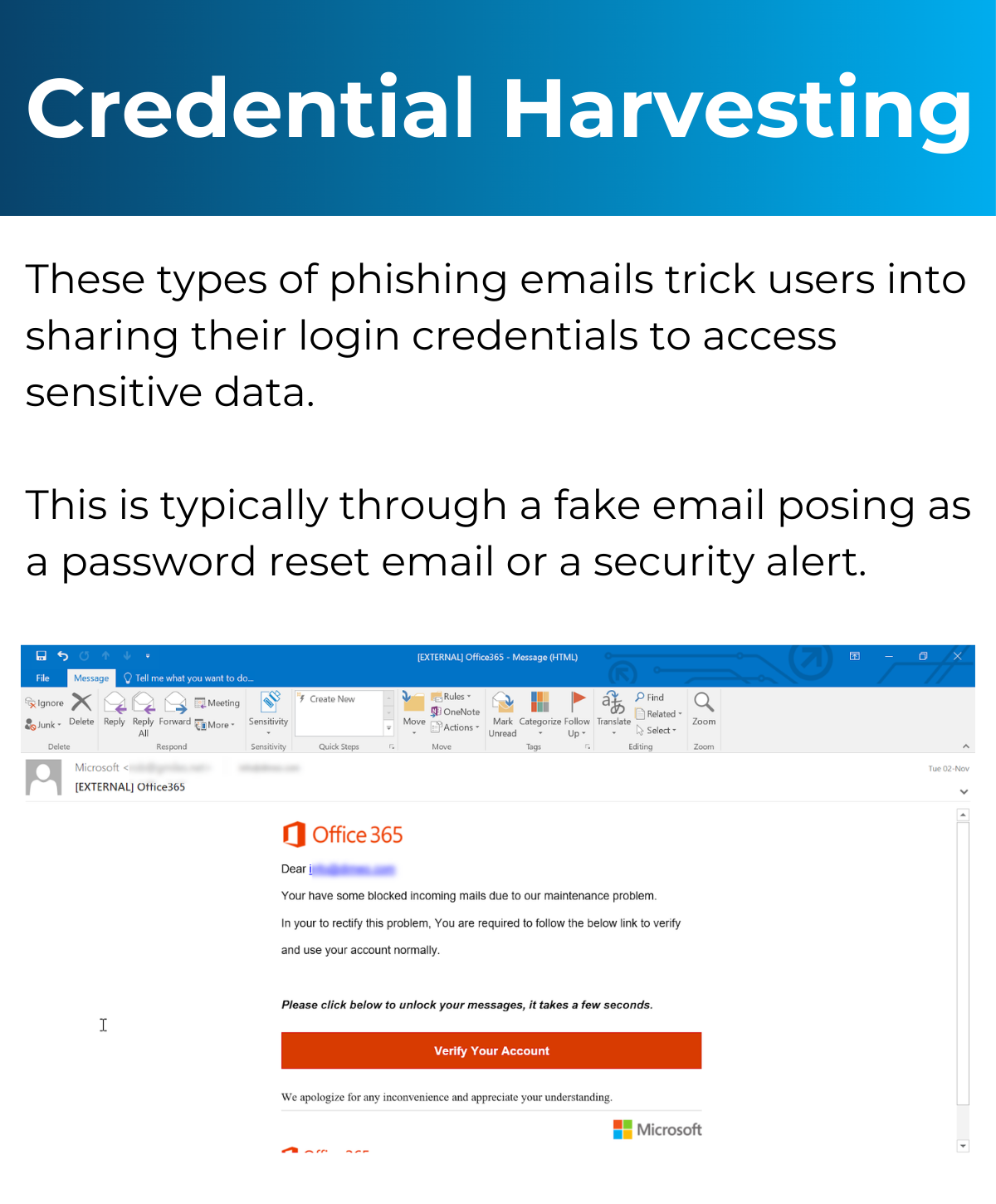
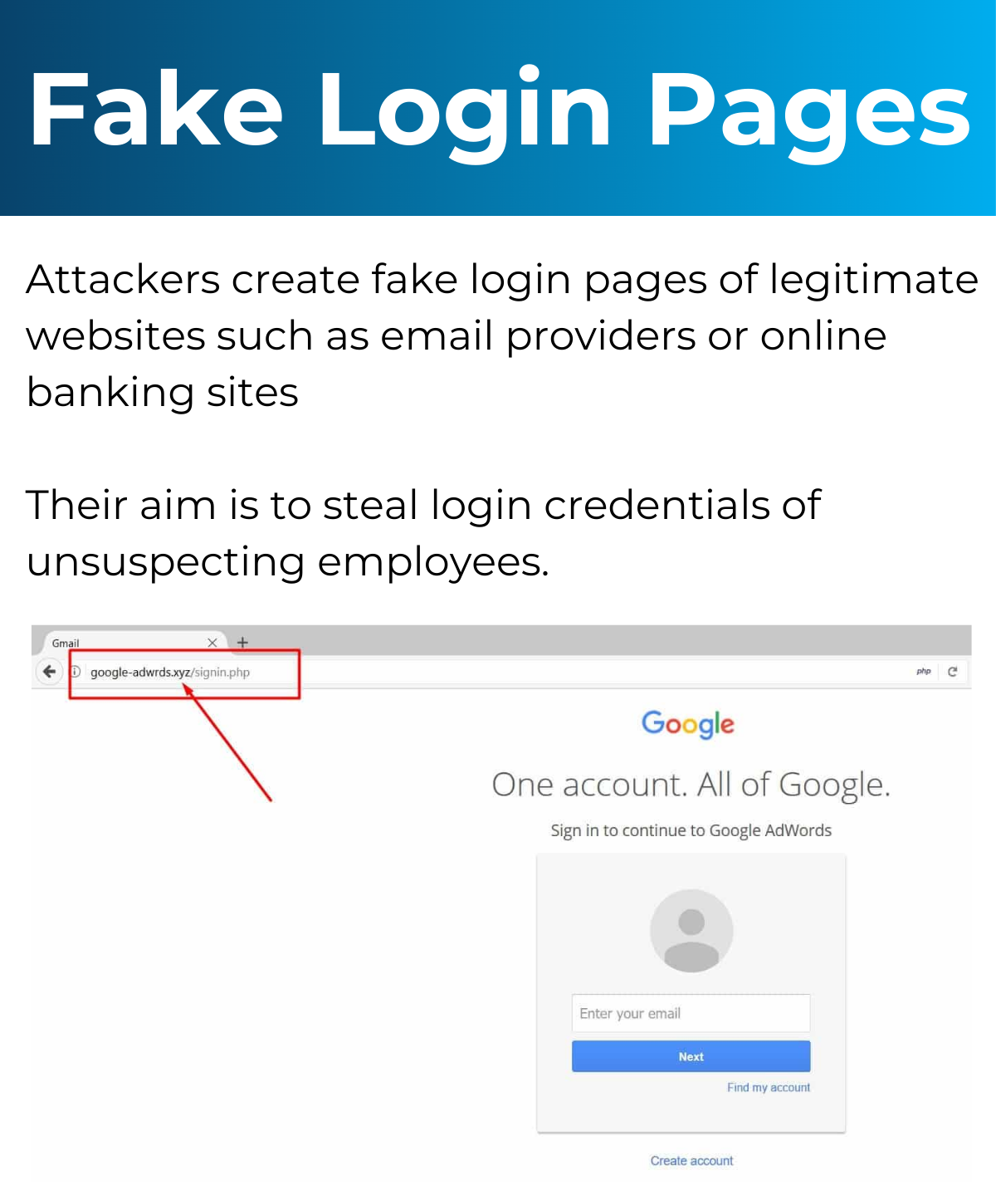
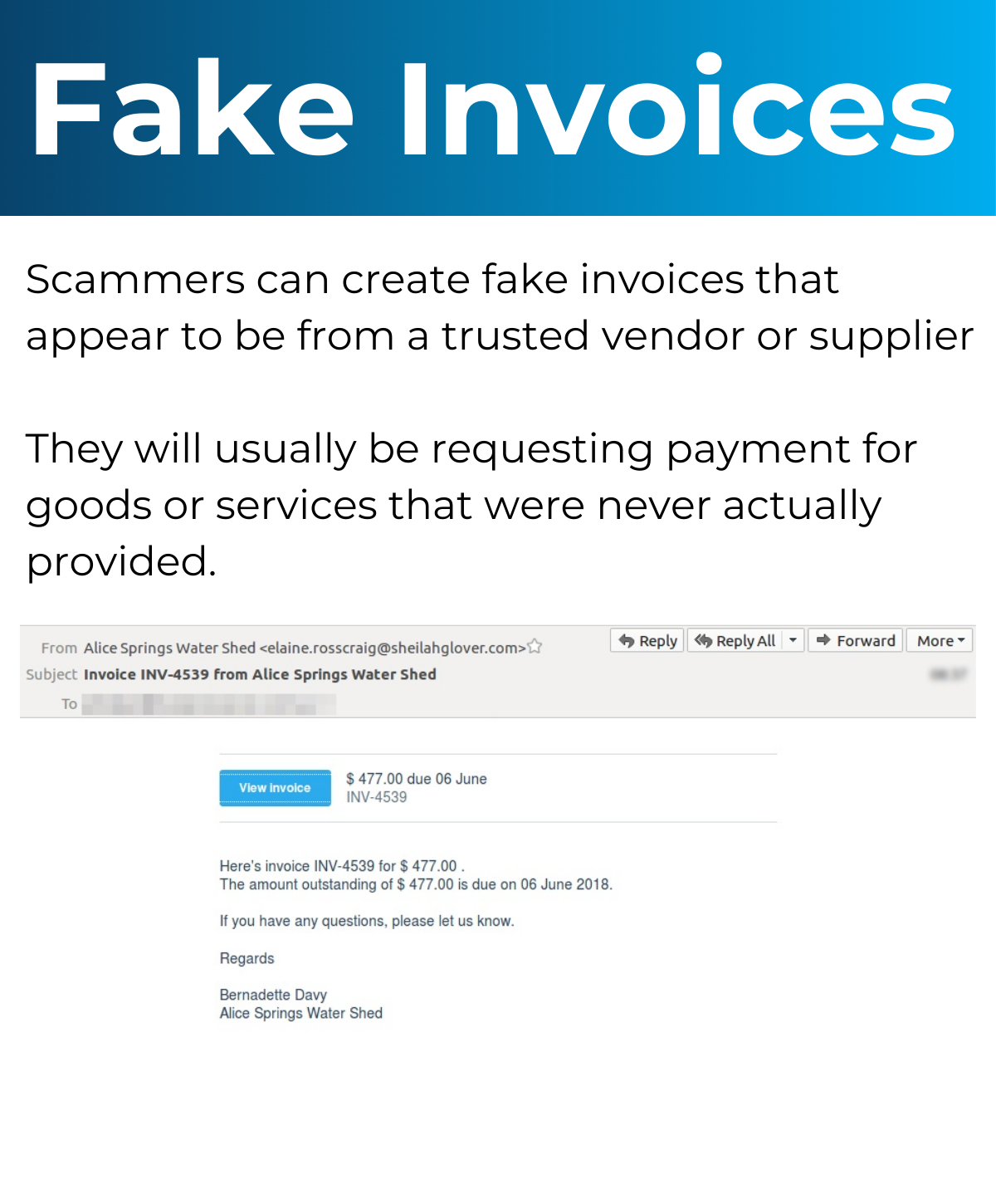
Types of Attacks You Could Experience
Below is information on the different attacks you could experience and an example of what that might look like. Click each image to learn what to be wary of.